
10 Smart Ways to Maximize Microsoft 365 for Your Business
Microsoft 365 is much more than just email and spreadsheets—it's an entire productivity suite built to improve teamwork, streamline workflows, and protect sensitive data. At KIS Technologies Inc., we help businesses fully harness these tools to improve efficiency and...

Samsung Data Breach: How to Protect Your Business Today
In an era where digital security is paramount, a recent breach at Samsung Germany has underscored the vulnerabilities that even tech giants face. A hacker, operating under the alias 'GHNA', leaked approximately 270,000 customer records from Samsung's ticketing system....

How Does DMARC Work?
Email security is a critical concern for businesses, as cybercriminals frequently use spoofing and phishing tactics to impersonate trusted domains. Without proper authentication measures, fraudulent emails can damage a company's reputation and lead to data breaches....
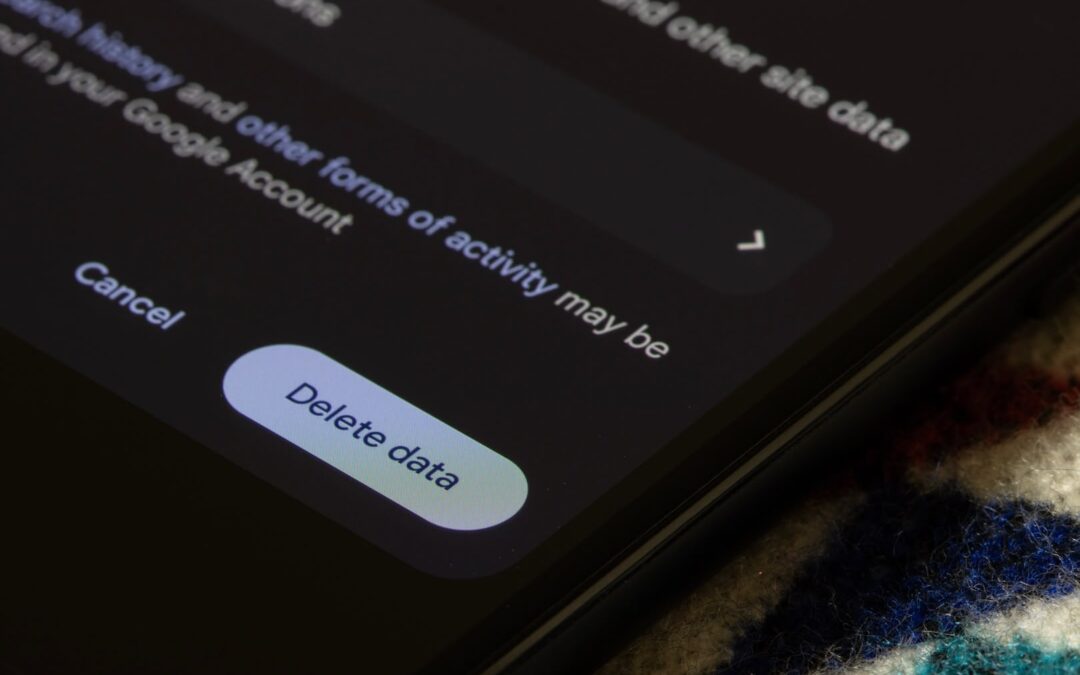
Secure File Storage and Transfer Best Practices
Imagine sending an important document, only to find out later that it was intercepted or leaked. Data breaches happen daily, exposing confidential files and causing financial losses. Without proper security measures, your sensitive information is at risk of being...

Good Neighbour Podcast with Jody Patfield of KIS Technologies Inc
Celebrating our 26th year of providing Digital office equipment such as photocopiers, printers, scanners and phone systems to local Businesses. Our business has expanded over the years, and now includes our Managed IT Services/Security Department, which provides...

What is a Data Breach?
Data breaches are making headlines more often than ever. Whether it’s a major corporation, a small business, or an individual, no one is completely safe from the risks of unauthorized data access. Imagine waking up one day to find out your personal information,...
